How To Create A Windows Application In C#
-
Table of Contents
- iProtecting your computer with Application Whitelisting
- 2How to merely allow certain Windows Applications to Run
- iiiHow to whitelist specific programs using Software Restriction Policies
- 4Tips when creating Path Rules
- 5Other types of Software Restriction Policy Rules
Protecting your reckoner with Application Whitelisting
In Windows it is possible to configure two different methods that determine whether an application should be allowed to run. The first method, known as blacklisting, is when you lot let all applications to run by default except for those yous specifically do non permit. The other, and more secure, method is called whitelisting, which blocks every application from running by default, except for those you explicitly allow.
With the wide distribution of computer ransomware and other malware infections and the loftier costs of recovering from them, a very stiff figurer protection method is whitelisting. This allows yous to block all programs by default then setup rules that specifically allow only certain programs to run.
Though easy to setup initially, whitelisting can be burdensome as you will need to add new rules every time you install a new plan or desire to allow a program to run. Personally, I feel if you are willing to put the time and effort into using whitelisting, the chances of a computer infection dissentious your computer becomes minimal.
This tutorial will walk you through setting up whitelisting using Software Restriction Policies so that only specified applications are able to run on your computer. Though this guide will be geared towards individual users, this aforementioned arroyo tin can be used in the enterprise by pushing these policies to a Windows domain.
How to but permit certain Windows Applications to Run
To get started white listing your applications you lot demand to open the Security Policy Editor, which configures the Local Security Policies for the machine. To practise this, click on the Outset button and then type secpol.msc into the search field as shown below.
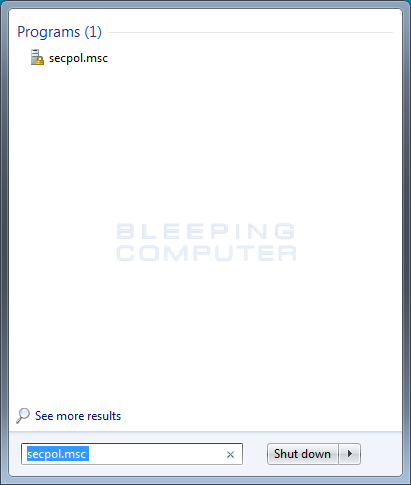
When secpol.msc appears in the search list, click on it to offset the Local Security Policy editor.
You should now see the Local Security Policy editor as shown beneath.
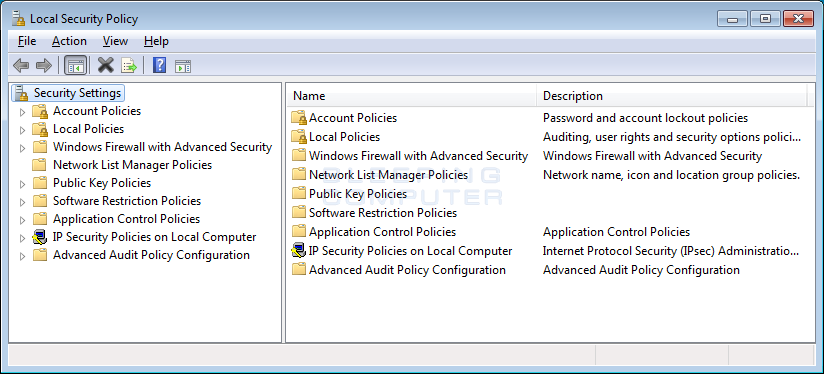
To begin creating our awarding whitelist, click on the Software Restriction Policies category. If you have never created a software restriction policy in the past, yous will see a screen similar to the one below.
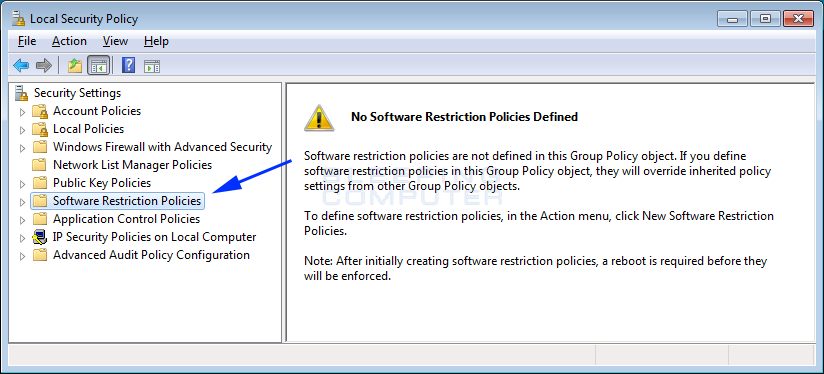
To create the new policy, correct click on the Software Restriction Policies category and select the New Software Restriction Policies option equally shown below.
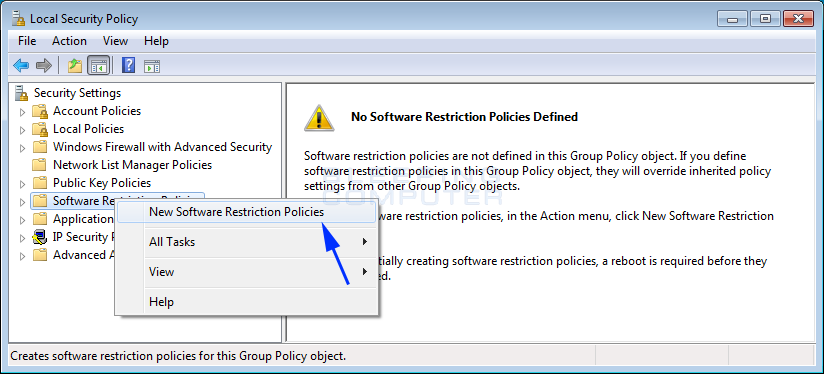
A new Software Brake Policy will now be created as shown below.
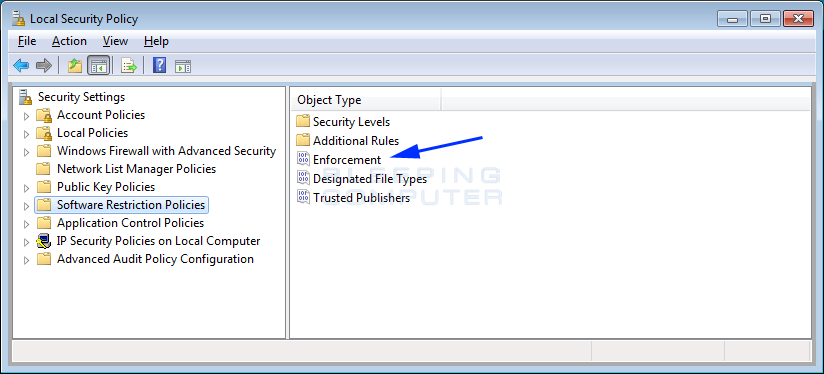
The first thing y'all need to do is configure the Enforcement department. This section allows united states of america to specify full general settings on how these brake policies volition exist configured. To get started, click on the Enforcement object blazon as indicated past the blue pointer above.
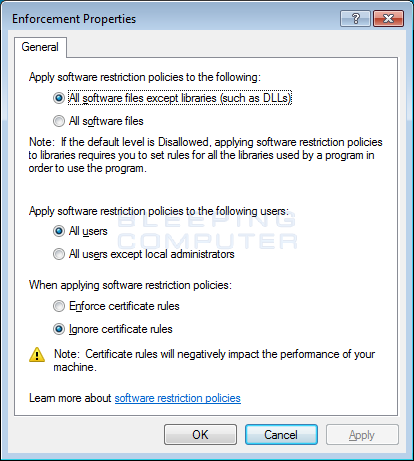
I suggest that you leave the settings like they are for at present. This allows y'all to create a strong policy, without the bug the may be caused by blocking DLLs. When yous are done configuring these settings, click on the OK push.
You will now exist back at the main Software Restriction Policies window as shown in Figure 5. We now want to configure what file types volition be considered an executable and thus blocked. To do this click on the Designated File Types object.
This will open the properties window for the designated file types that volition be considered equally an executable and therefore blocked past the software restriction policy that you are creating.
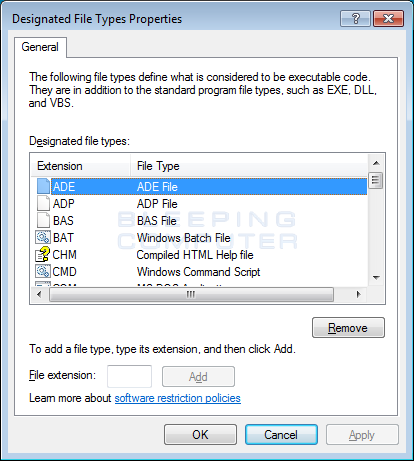
Unfortunately, the above the list is non as exhaustive as you would like and includes an extension that should be removed. First, curl through the to a higher place list of file extensions and remove the LNK extension from the list. To remove the extension, left-click on it in one case and then click on the Remove button. If you do non remove this extension, so all shortcuts will fail to work afterward you lot create our whitelist.
Now you lot want to add together some actress extensions that are known to be used to install malware and ransomware. To add an extension, simply add it to the File Extension field and click on the Add button. When adding an extension, do not include the period. For case, to exclude powershell scripts, you would enter PS1 into the field and click on the Add together button.
Delight add the following extensions to the designated file types:
| Extensions to add to the File Type List | |
|---|---|
| PS1 | SCT |
| JSE | VBE |
| VBS | WSF |
When yous are done adding the to a higher place extensions, click on the Apply button and then the OK button.
Nosotros will now exist back at the main Software Restrictions Policy section as shown in Figure eight below. At this point, you demand to configure the default policy that decides whether the file types configured in effigy 7 will be automatically blocked or allowed to run. To exercise this, click on the Security Levels choice as indicated by the blueish arrow below.
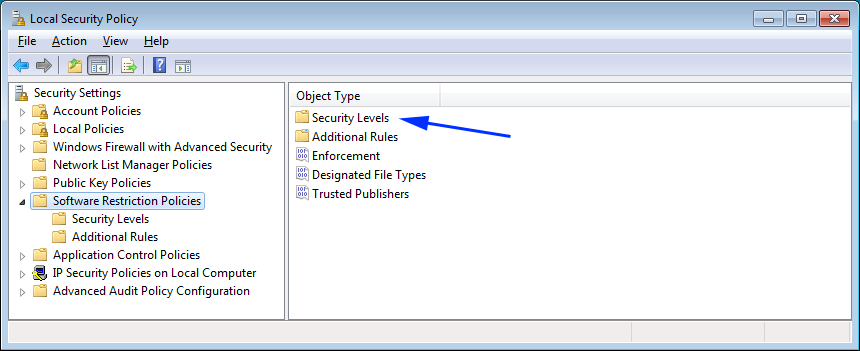
When you double-click on the Security Levels category, you will be brought to the screen below that has 3 security levels yous can employ to your software restriction policies.
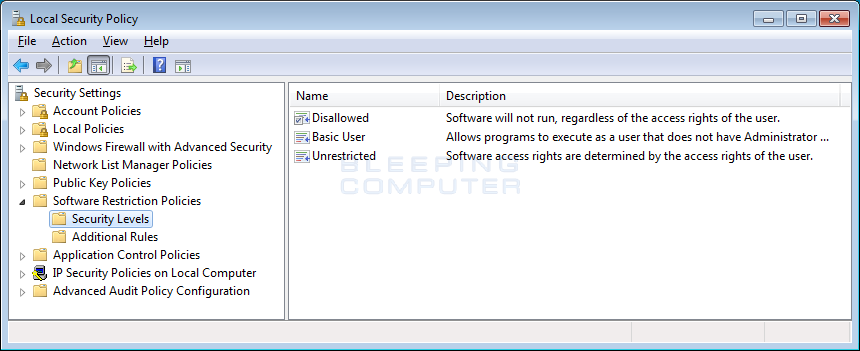
In order to select which level should exist used, you lot need to double-click on the detail level and set it as the default. Beneath are the descriptions for each blazon of security level.
Disallowed: All programs, other than those you allow by the rules you will configure, will not be immune to run regardless of the admission rights of the user.
Basic User: All programs should execute as a normal users rather than equally an Administrator.
Unrestricted: All programs can be run as normal.
Since you want to block all applications except those that y'all white list, you want to double-click on the Disallowed button to enter its backdrop screen as shown beneath.
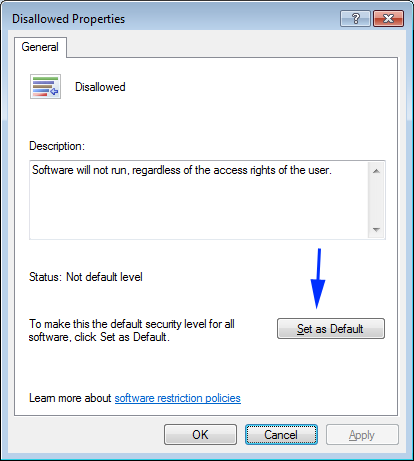
In the to a higher place properties screen, to make information technology so all applications volition at present be blocked past default, please click on the Set as Default button. So click on the Utilize and OK buttons to exit the properties screen.
We will now be dorsum at the Security Levels list and almost every program will now be blocked from executing. For instance, if you try to run Internet Explorer, you will receive a bulletin stating that "This plan is blocked by group policy." every bit shown below.
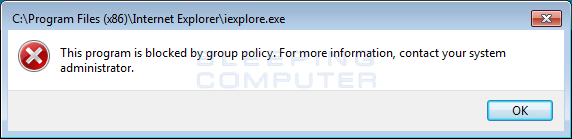
At present that you take configured Windows to cake all applications from running, you demand to configure rules that let your legitimate applications to run. The next section will explain how to create path rules so that the applications y'all wish to allow to run are whitelisted.
How to whitelist specific programs using Software Restriction Policies
If you followed the previous steps, Software Brake Policies are at present enabled and blocking all executables except those located under C:\Programme Files and C:\Windows. Those two directories are automatically whitelisted by two default rules that are created when you setup Software Restriction Policies.
Obviously, in order to have a properly working machine you need to now allow, or whitelist, other applications. To do this, you need to create additional rules for each folder or application you wish to allow to run. In this tutorial, we are going to add a new Path Rule for the C:\Plan Files (x86) folder as that needs to likewise be whitelisted for 64-bit versions of Windows.
While in the Local Security Policy editor, click on the Additional Rules category nether Software Brake Policies every bit shown below.
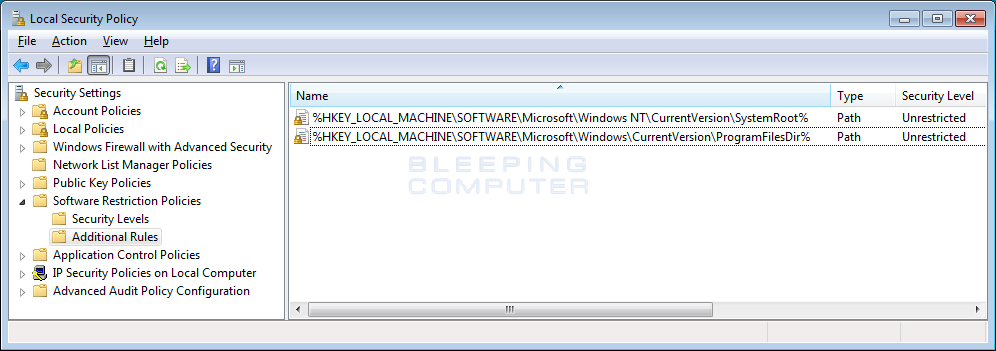
Every bit y'all can see from above, there are already two default rules configured to permit programs running under C:\Windows and C:\Program Files to run. If you are running a 64 chip version of Windows you now want to add a further rule that will let programs under the C:\Program Files (x86) folder to run as well.
To do this, right-click on an empty portion of the right pane and click on New Path Rule... every bit shown below.
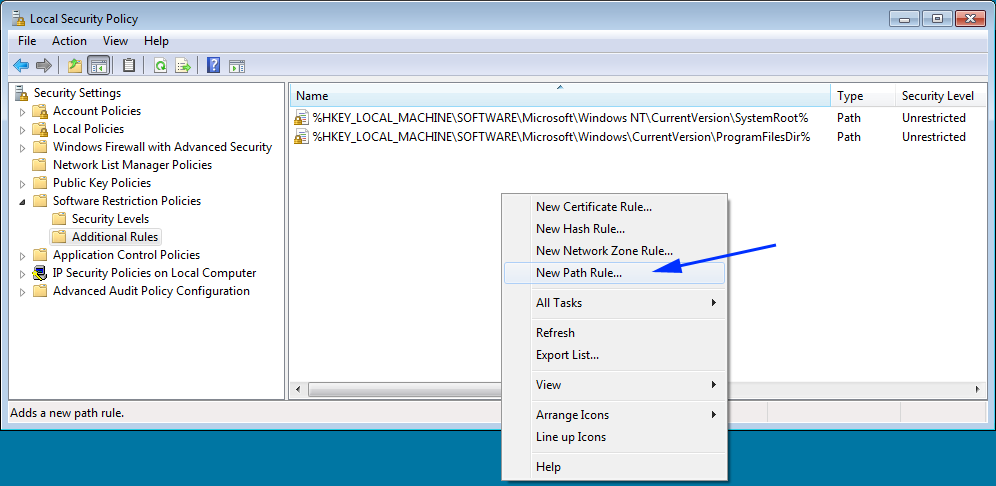
This will open up the New Path Rule Properties dialog equally shown below.
Equally yous want to create a path rule for C:\Program Files (x86), you should enter that path into the Path: field. Then brand sure the Security Level is set to Unrestricted, which means the programs in it are allowed to run. If you wish, you can enter a short description explaining what this rule is for in the Description field. When you are finished, the new rule should wait like the ane beneath.
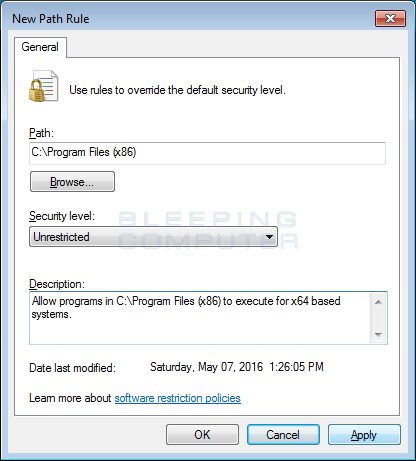
When you are fix to add this rule, click on the Apply and then OK button to make that rule active.
You will now be dorsum at the Rules page and the new C:\Program Files (x86) rule will exist listed and programs located in that binder will now exist allowed to run.
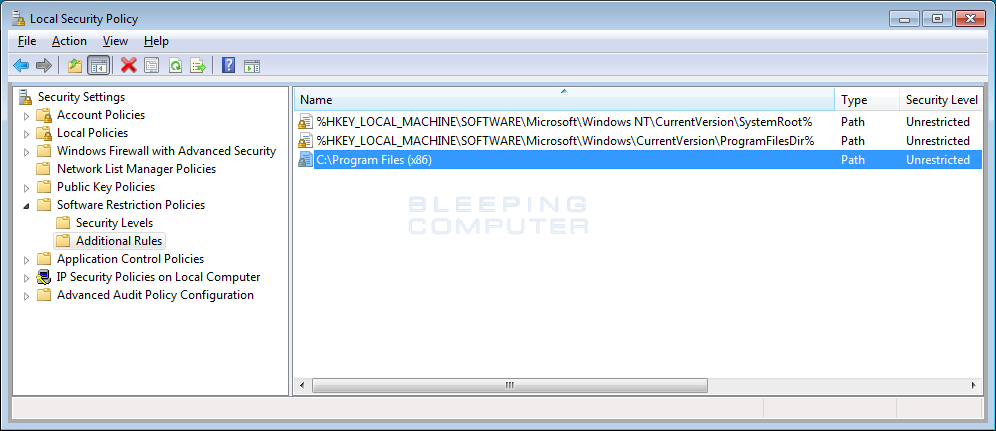
You now demand to brand new rules for other programs that you wish to permit to run in Windows. For case, if yous play games with Steam, you should follow the steps higher up to add an unrestricted dominion for the C:\Program Files\Steam\ folder.
In the next ii sections, I have provided tips and and other types of rules that can be created to whitelist programs. I suggest y'all read it to take reward of the full power of Software Restriction Policies.
As always, if y'all demand assistance with this process, please do not hesitate to inquire in our tech support forums.
Tips when creating Path Rules
When adding a path dominion that is a folder, it is of import to note that whatsoever subfolder volition as well be included in this path rule. That means if you lot have applications stored in C:\MyApps and create a path rule that folder specifies that folder is unrestricted, and then all subfolders will be allowed to run every bit well. And then not only will C:\MyApps\myapp.exe be immune to run, just also C:\MyApps\games\gameapp.exe is allowed to execute besides.
To arrive easier when creating rules, it is also possible to utilize wild cards to aid y'all specify what programs should be allowed to run. When using wild cards, you tin apply a question marker (?) to denote a unmarried wildcard character and a asterisk (*) to denote a serial of wildcard characters.
For example, if yous have a folder of executables that y'all wish to whitelist, you lot can do so by using a wildcard path dominion similar this: C:\MyApps\*.exe. This dominion would allow all files that end with .exe to execute, but non permit executables in subfolders to run. You can as well use a path rule that specifies a single wildcard character similar C:\MyApps\app?.exe. This rule would allow C:\MyApps\app6.exe to run, but non C:\MyApps\app7a.exe to run.
It is also possible to use environment variables when creating path rules. For example, if you wish to allow a folder under all the user profiles, yous can specify a dominion similar %UserProfile%\myfolder\*.exe. This would merely allow executables nether that particular folder to execute, but would aggrandize %UserProfile% to the correct binder for whoever is logged into the computer.
Concluding, just not least, if you wish to run executables from a network share, then you demand specify the full UNC path in the dominion. For example, \\Dev-server\Files.
Other types of Software Brake Policy Rules
When creating rules, it is likewise possible to create other rules chosen Document Rules and Hash Rules. These rules are described below.
Certificate Rule: A document rule is used to allow whatever executable to run that is signed by a specific security document.
Hash Rule: A hash rule allows you to specify a file that tin can exist run regardless of where it is located. This is washed by selecting an executable when creating the dominion and certain information will be retrieved by SRP and saved as part of the rule. If any other executables on the computer match the stored file hashed and information, it will exist immune to run.
Annotation: Microsoft has stated that Certificate Rules could cause performance issues if used, so only use them if absolutely necessary.
Source: https://www.bleepingcomputer.com/tutorials/create-an-application-whitelist-policy-in-windows/
Posted by: mckinnongreaboy.blogspot.com

0 Response to "How To Create A Windows Application In C#"
Post a Comment